Securonix
An analytics-driven platform that delivers threat detection and response in a cloud-native architecture that scales as you grow.
Unified Platform for Complete Security Monitoring
Ready to stay ahead of the advanced threats without all of the complex infrastructure? Unlock complete security visibility powered by advanced analytics, with zero infrastructure to manage.
SIEM: Achieve advanced detection at scale. Built on big data, our SIEM combines log management, analytics, automation, and response capabilities into a single, unified solution. Learn More
UEBA: Eliminate alert fatigue with security analytics. Our solution leverages sophisticated machine learning and behavior analytics to help you prioritize and mitigate high-risk incidents versus low-value alerts. Learn More
OPEN XDR: Empower your security teams with complete visibility. XDR helps your analysts efficiently identify, investigate, and respond to hard-to-detect threats in your environment. Learn More
Read the Data Sheet
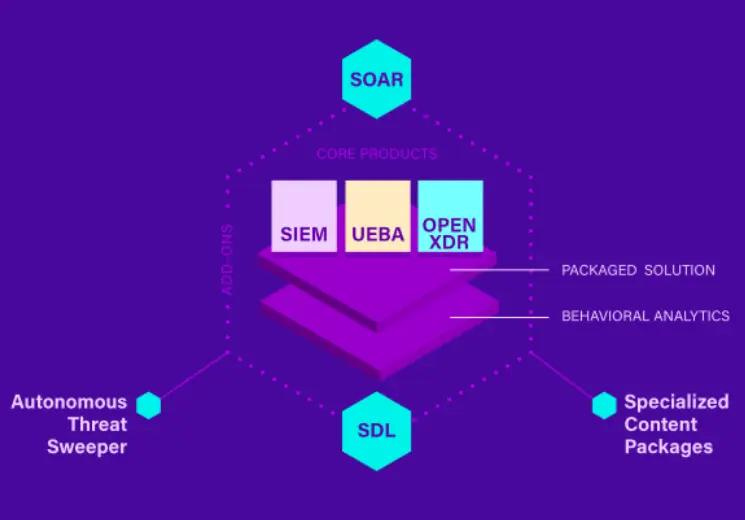
Security Analytics and Operations Platform
The Securonix Security Analytics and Operations Platform combine log management; user and entity behavior analytics (UEBA); next-generation security information and event management (SIEM); extended detection and response (XDR); and security orchestration, automation, and response (SOAR) into a complete, end-to-end security operations platform.
The Securonix platform delivers unlimited scale, powered by advanced analytics, behavior detection, threat modeling, and machine learning. It increases your security through improved visibility, actionability, and security posture while reducing management and analyst burden.
Why the Securonix Platform?
Unified
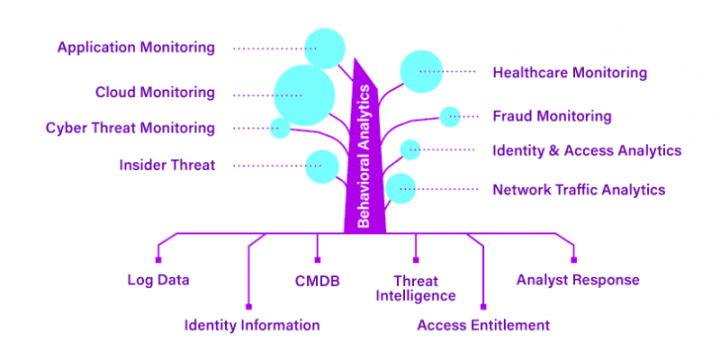
One Platform, Many Use Cases
Insights
Collective Defense with Securonix Threat Labs
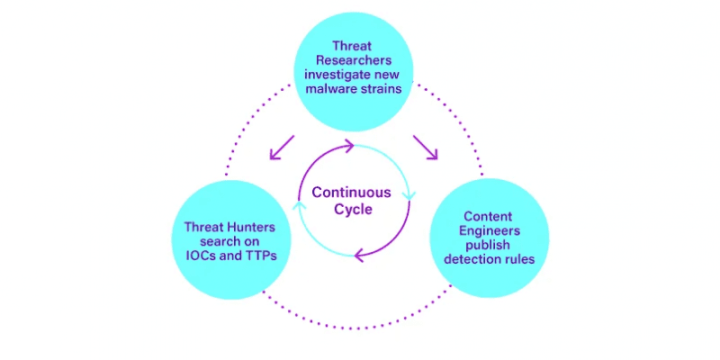
Integrated

Vast Technical Partner Ecosystem
Securonix is proud to join forces with some of the most prominent technology companies in the world to provide you with seamless visibility and response across diverse technologies.
Solution Briefs
Threat Hunting with Securonix
Securonix Next-Gen SIEM allows you to more quickly detect advanced and sophisticated threats that would otherwise remain in your network, undetected.
Download this solution brief to find out more.
Securonix Identity and Access Analytics
Securonix integrates with every major IAM and IGA solution to deliver a continuous stream of identity analytics and intelligence allowing for:
– Improved access management compliance through user and resource-centric views of access risk.
– Automated access cleanup and risk-based certification.
– Streamlined, risk-based access request processes
Download this solution brief to find out more.
Security Monitoring for Google Cloud Platform
Download this solution brief to find out more.
Securonix Security Monitoring for Microsoft Azure
Download this solution brief to find out more.
Securonix Integration for Service Now
Download this solution brief to learn more about how Securonix seamlessly integrates with your ServiceNow Service Management solution, helping you smoothly track and manage your incidents, problems, changes, and service requests.







