Detect cyber-attacks and minimize data loss
Over the past few years, several retail organizations have been hit with high-profile data breaches that have left millions of customers’ credit card details and personal information exposed. Retailers will continue to be prime targets for motivated cyber criminals targeting sensitive and lucrative customer data, and must take steps to secure delicate information.
Designed to help retail organizations properly configure and monitor their IT environment.
LogRhythm’s Retail Cyber Crime Security Analytics Suite was specifically designed to help retail organizations properly configure and monitor their IT environment to achieve a complete forensic view into anomalous and malicious activity.
This includes everything from activity on point-of-sale (POS) system endpoints to the payment processor, as well as back-office and network infrastructure. The Retail Cyber Crime Suite provides the continuous monitoring needed to detect behavioral changes and attacks within the cardholder data environment, expediting remediation and breach containment, and minimizing data loss and brand exposure.
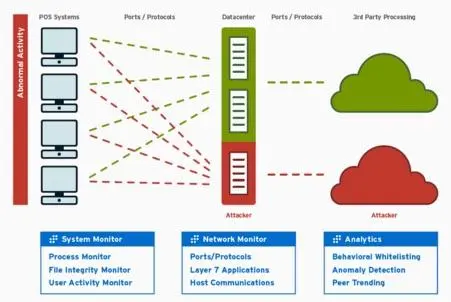
Benefits of LogRhythm’s Retail Cyber Crime Security Analytics Suite include:
- Correlate all data from highly distributed retail environments for a complete view into payment processing chain
- Establish a “gold standard” to detect anomalous and malicious activity on POS systems
- Quickly identify early indicators of cyber-attacks on the payment processing chain to effectively detect and contain breaches
Additional Resources
If you would like more information on LogRhythm, contact us today!




















