Overview
IBM Security® QRadar® EDR, formerly ReaQta, remediates known and unknown endpoint threats in near real time with easy-to-use intelligent automation that requires little-to-no human interaction. You can make quick and informed decisions with attack visualization storyboards and use automated alert management to focus on threats that matter. Advanced continuous learning AI capabilities and a user-friendly interface put security staff back in control and help safeguard business continuity.
Benefits
Closer Look
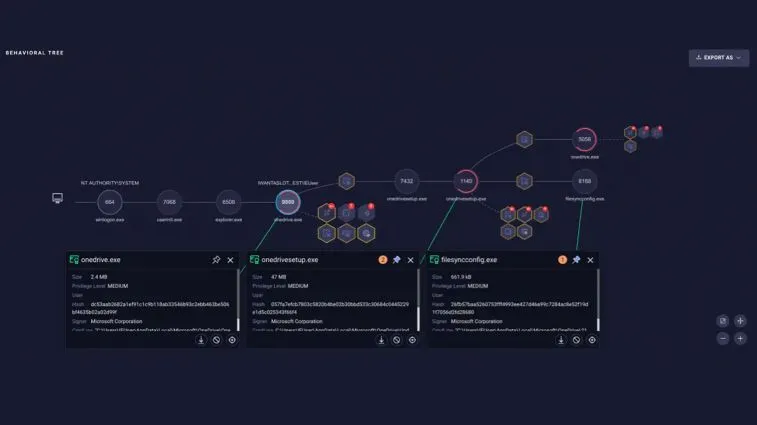
Behavioral tree
A behavioral tree provides full alert and attack visibility. A user-friendly visual storyline helps analysts speed up their investigation and response. From here, analysts can also access containment controls and three stages of incidence response: triaging, response and protection policies.
Cyber Assistant alerts
The Cyber Assistant, an AI-powered alert management system, can autonomously handle alerts, reducing analysts’ workloads.
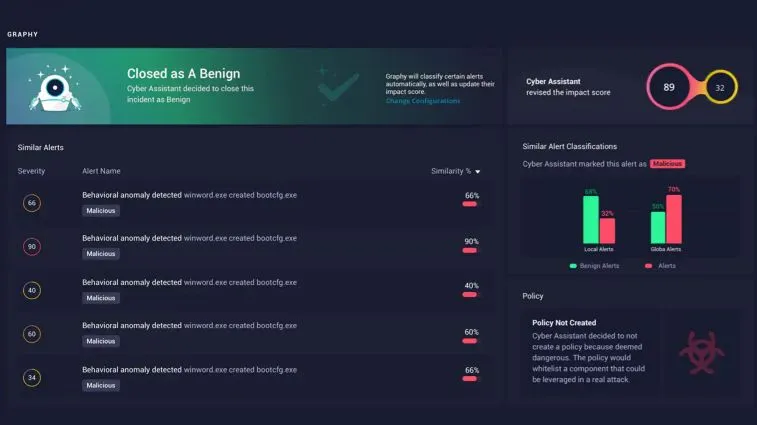
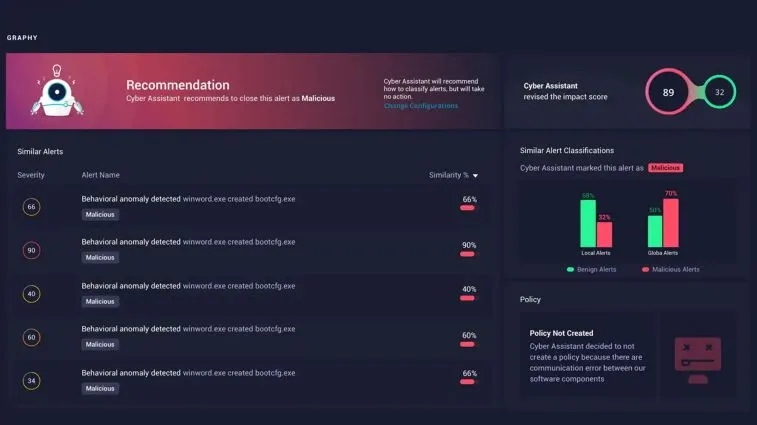
Cyber Assistant recommendations
The Cyber Assistant learns from analyst decisions, then retains the intellectual capital and learned behaviors to make recommendations and help reduce false positives.
Custom detection strategies
Detection Strategy (DeStra) scripting allows users to build custom detection strategies—beyond preconfigured models—to address compliance or company-specific requirements without the need to reboot the endpoint.
QRadar® MDR
Have IBM experts manage your Endpoint Detection & Response. 24×7 managed endpoint detection and response—powered by AI, delivered by IBM Managed Security Services.
Full alert management
All detections (low, medium, high severity) are investigated, analyzed and managed, without extra effort from the local security team.
Rapid threat containment
Analysts will respond against active threats by way of termination and removal of malicious files or processes, creation of blocking policies or by isolating the endpoints.
Proactive threat hunting
Proactive threat hunting is powered by X-Force threat intelligence and done continuously by the QRadar EDR console, which searches for potential indicators of attack and compromise.
If you would like more information on IBM QRadar, contact us today!

