Security within reach
IBM Security® QRadar® Log Insights can help you gain complete visibility over your exponential and continuously growing digital footprint. Designed to address security observability needs with simple data ingestion, rapid search and powerful visualization, it’s optimized to perform analytics on data with greater efficiency and to provide faster insights.
QRadar Log Insights is powerful enough to extract, investigate and pull data from anywhere, and it can quickly perform multiple, concurrent searches on large data subsets in seconds. We infused the tool with smart, interactive dashboards and analytics to help you detect, investigate and plan action against threats faster.
Benefits
Why QRadar Log Insights

Unified analyst experience built to increase productivity
Actionable dashboards and powerful search UX with built-in threat intelligence enrichment, federated search and case management allow more time for strategic analysis and threat hunting. The unified analyst experience is built specifically for the demands of today’s security operations and hybrid cloud environments.
More than just a log manager
Investigate
What do I hunt?
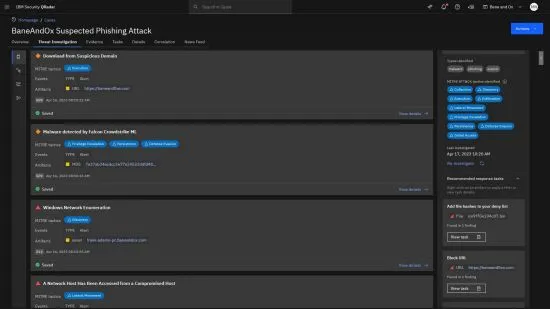
Stop spending hours researching the latest threats. QRadar Log Insights helps you find threats by using the latest malicious IP addresses, URLs and malware file hashes. It applies threat intelligence to both manual investigations and cases automatically created QRadar Log Insights leverages Sigma Rules and uses Kestrel Threat Hunting as the AI base component. The AI model acts as a security analyst who knows exactly what to hunt for.
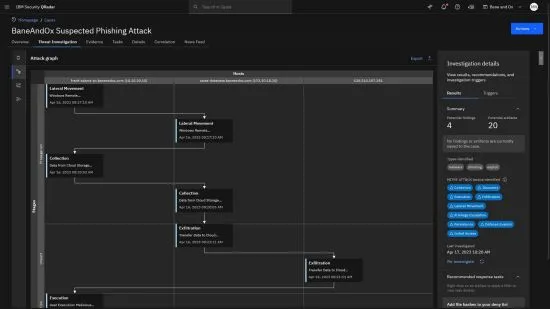
Analyze
What does it mean?
After threat intelligence capabilities identify risky behavior or critical threats, QRadar Log Insights aligns the data to the MITRE ATT&CK framework, which reduces the triage process to minutes. You can quickly identify which TTP’s are used and filter through the supporting data for more information and details.
Take Action
What do I need to do about it?
Powered by AI, QRadar Log Insights provides recommendations based on industry best practices should your system identify a threat.

Features
Elastically scalable ingestion
Scale terabytes of data in minutes with low-latency ingestion on the AWS Cloud.
Advanced intuitive KQL
Build, troubleshoot and minimize detection time with KQL.
Data explorer
Find the answers you need fast from streaming data.
Grafana plug-in
Fast and flexible. Visualize your data anyway you want with dashboards that are most meaningful to you.
Frequently asked questions
QRadar Log Insights includes the ability to detect threats by using threat intelligence where discovered indicators result in new alerts, and from scheduled searches run against the data warehouse. Log Insights also includes the QRadar unified analyst workflow that enables users to quickly triage and respond to alerts.
Yes, QRadar Log Insights can generate alerts from KQL and STIX queries, as well as from threat intelligence updates by using threat intelligence insights.
Yes, Log Insights goes beyond a standard log management product to provide recommended actions according to search-based alerts and automated investigation functionalities.
A SIEM will collect, analyze and correlate data to detect threats. Log Insights will ingest, normalize and store data in one location for analysts to easily search and make decisions about an environment’s health. Essentially, a SIEM provides actionable alerts whereas a log manager brings data together, allows for quick search and offers flexible storage options at a lower price point.
Users must acquire the license and install Grafana and then configure the QRadar KQL Plugin.
Related Products
IBM Security® QRadar® SIEM
IBM Security® QRadar® EDR
IBM Security® QRadar® SOAR
IBM Security® Intelligence Operations and Consulting Services
If you would like more information on IBM QRadar, contact us today!
